Discuz!系统的_xss_check()函数原本的意义是为了论坛安全,防止XSS攻击,一般网站使用是不会出现什么问题的,但是有些网站要接入第三方接口,当第三方接口向本站post数据的时候就会报”您当前的访问请求当中含有非法字符,已经被系统拒绝”,本文介绍一种简单的修改方法避免此错误。
解决方案如下:
\source\class\discuz的discuz_application.php
查找
private function _xss_check() {
static $check = array('"', '>', '<', '\'', '(', ')', 'CONTENT-TRANSFER-ENCODING');
if(isset($_GET['formhash']) && $_GET['formhash'] !== formhash()) {
system_error('request_tainting');
}
if($_SERVER['REQUEST_METHOD'] == 'GET' ) {
$temp = $_SERVER['REQUEST_URI'];
} elseif(empty ($_GET['formhash'])) {
$temp = $_SERVER['REQUEST_URI'].file_get_contents('php://input');
} else {
$temp = '';
}
if(!empty($temp)) {
$temp = strtoupper(urldecode(urldecode($temp)));
foreach ($check as $str) {
if(strpos($temp, $str) !== false) {
system_error('request_tainting');
}
}
}
return true;
}
替换为:
private function _xss_check() {
$temp = strtoupper(urldecode(urldecode($_SERVER['REQUEST_URI'])));
if(strpos($temp, '<') !== false || strpos($temp, '"') !== false || strpos($temp, 'CONTENT-TRANSFER-ENCODING') !== false) {
system_error('request_tainting');
}
return true;
}
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END
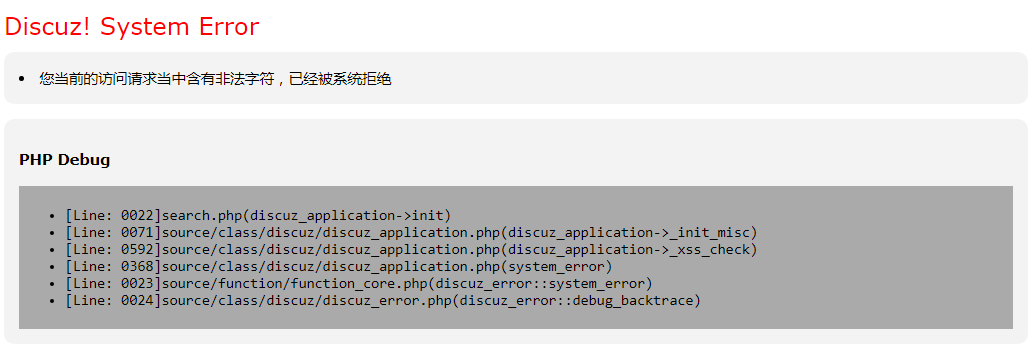

![图片[1]-Discuz!您当前的访问请求当中含有非法字符,已经被系统拒绝解决办法-下雪啦资源网](https://www.xiaxuela.com/wp-content/uploads/2020/08/ae7f263e0267a63-1024x342.png)



![苹果cms使用火车头发布数据报错:“SQLSTATE[22001]:String data,right truncated:1406 Data too long for column ‘vod_blurb’ at row 1”-下雪啦资源网](https://www.xiaxuela.com/wp-content/uploads/2020/12/da6b8ce280dece1-300x95.png)






暂无评论内容